Intro
It’s 10:30PM on a Sunday night, and I’m wondering what to do with the last few hours of the weekend. Not feeling like working on project code and digging for bug bounty treasure is sounding tedious at the moment. A CTF however sounds like a good time, and a quick trip over to ctftime.org show there’s a CTF ongoing!
RGB CTF 2020
Theres a few categories here:
Beginner - Cryptography - Forensics/OSINT - Misc - Pwn/Rev - Web - [ZTC]
Time is limited so I decided to play my strongest hand and tackle mostly web.
Before we get to web, it’s important to hit the warmups.
Beginner
Joke Check
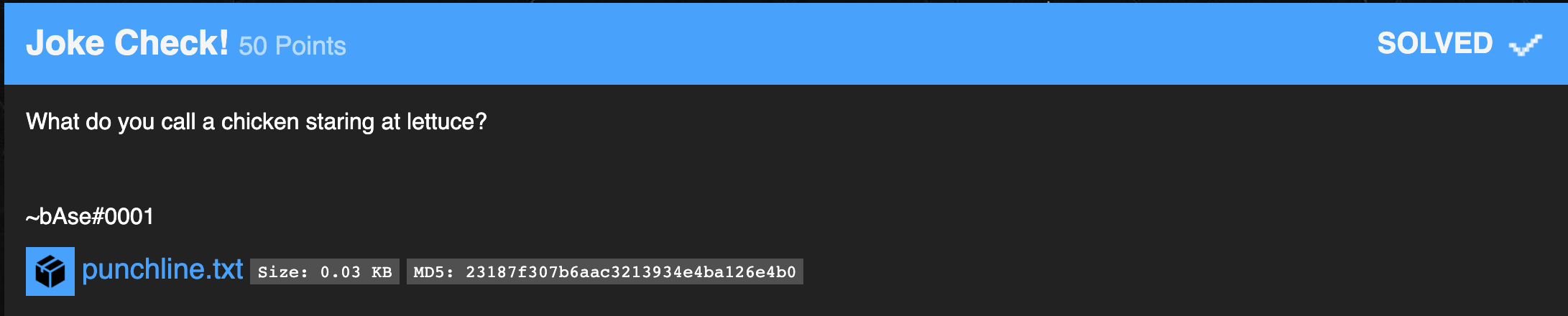
The punchline.txt file contains a single line, and its immediately apparent its a ROT13 cipher.
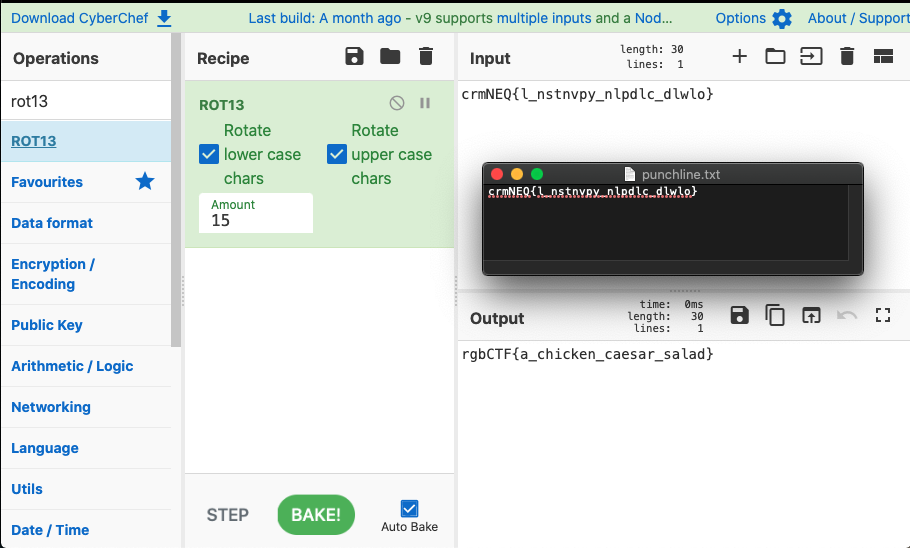
There is an absolutely awesome tool called CyberChef that was recommended to me at the Defcon OpenCTF a while back, and it has been useful in every CTF since.
If we toss in the Cipher we can see at Rotating 13 it doesnt unveil the answer, bumping that up to 15 however yields the flag.
Web
There was a total of 5 web challenges and they all packed a pretty good punch. With the time constraint I only managed to solve the first two due to a lucky commonality. The fourth challenge seemed tenable but I ran out of time before I got to a proper solution, I’m really looking forward to reading that writeup.
Type Racer
Type racer was actually the second challenge but I wound up solving this web challenge first due to my familiarity with the type-racer game itself. After all the time I spend building a mechanical keyboard I love to take it on type-racer for a good race.
Frequently I find myself faced with a prompt to validate my humanity lest I be cheating. This gave me an idea for a starting point with this challenge.
The javascript for the challenge is heavily obfuscated, it would burn what little time I have trying to deobfuscate it. Instead with the real type-racer’s cheating in mind I sought to create some javascript specific to this type-racer that I could drop in the console to type it all at a record pace for me.
To get started I opened up the browsers javascript debugger and set a break point to step through the type-racer challenge in hopes of identifying the array of words to read so I could then select the input field and loop over the array of values dropping them in.
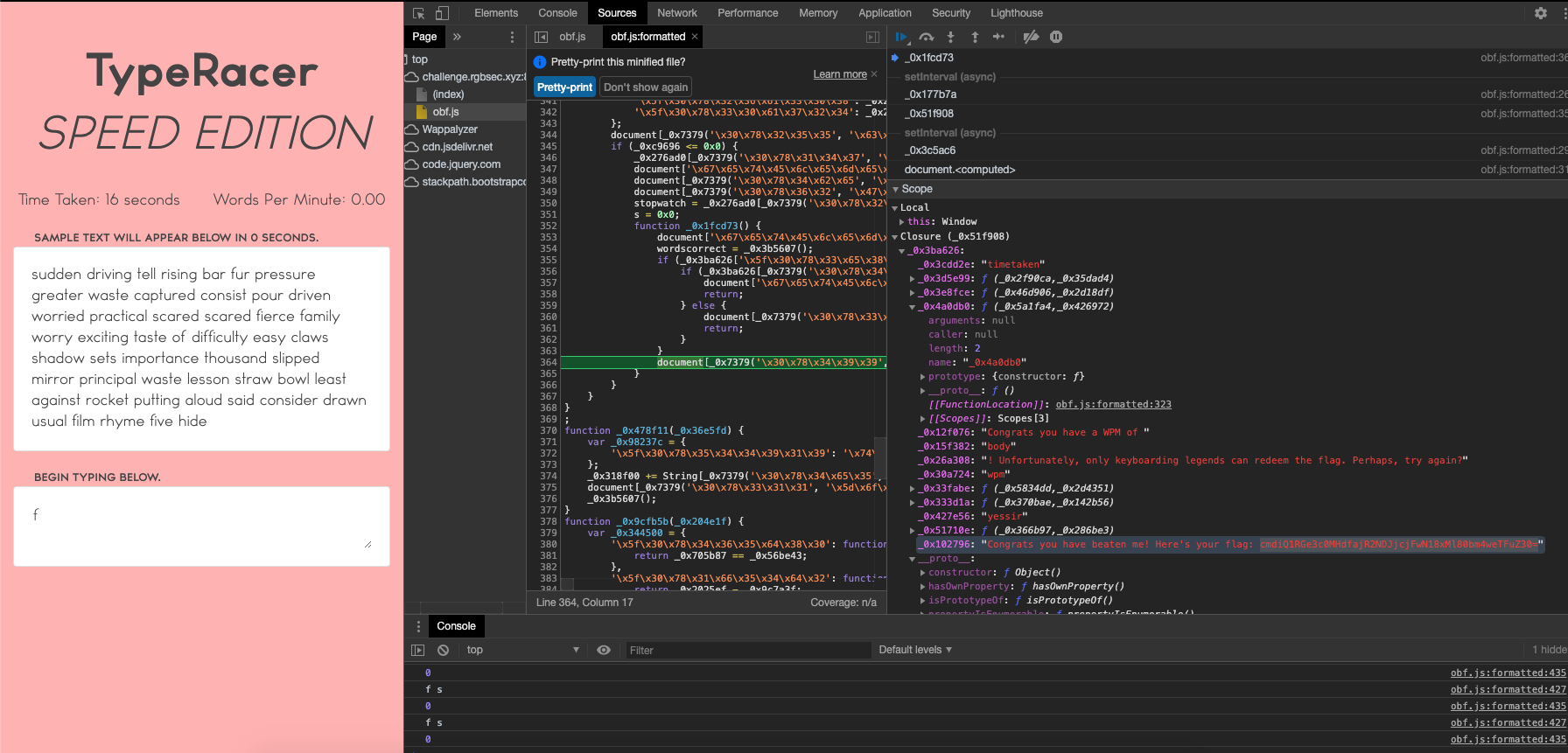
Lo and behold while stepping through it with the debugger, one of the local values caught me eye, sitting next to the victory message was a base64 encoded value that happened to be the flag.
Tic Tac Toe
Tic Tac Toe was actually the first challenge in this category, and the dev definitely did their work in ensuring the best outcome of a fair match was going to be a draw.
Armed with the thought of the debugger outing the value contained in a local variable on the type-racer challenge, I opted to try the same here.
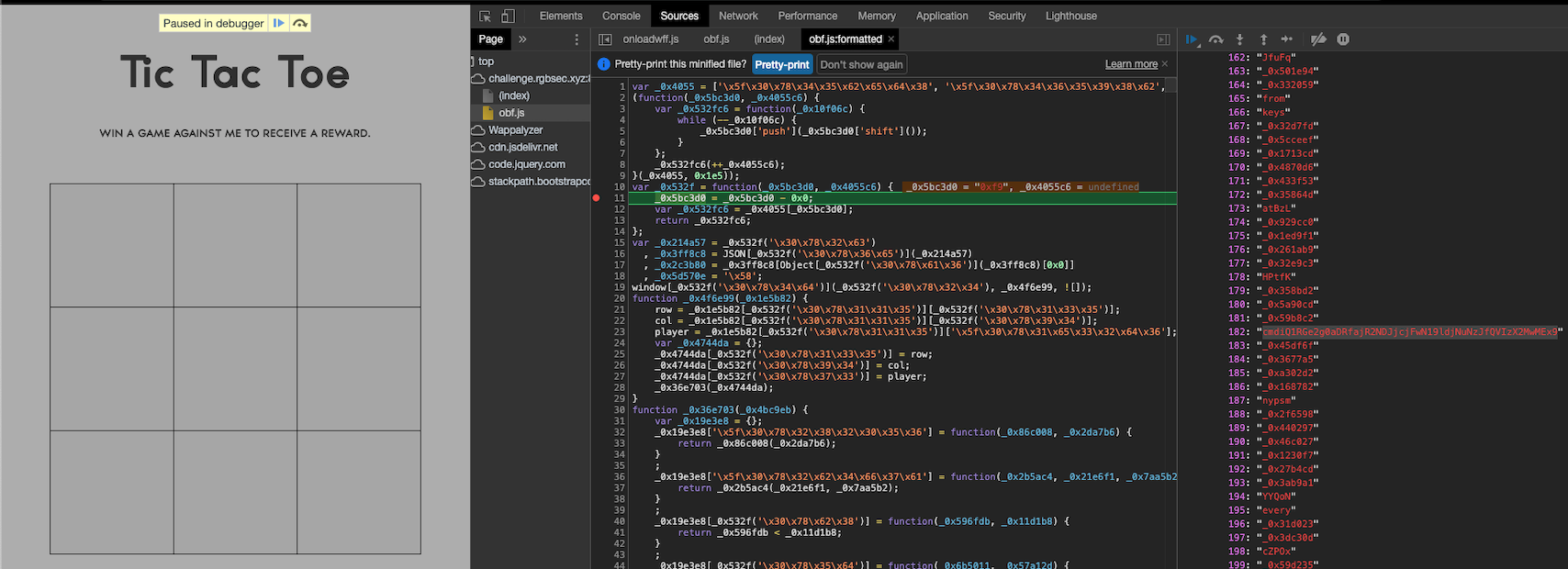
With a little scrutiny I was able to identify a suspicious looking base64 value that was the flag.
Not entirely sure if this is how the creators intended them to be solved, but hey it worked and thats what matters.
Cryptography
By this point I’m about out of time to spend on the CTF. After throwing in 2.5 hours Sunday evening, I came in with 30 minutes before the end of the CTF to solve one more challenge.
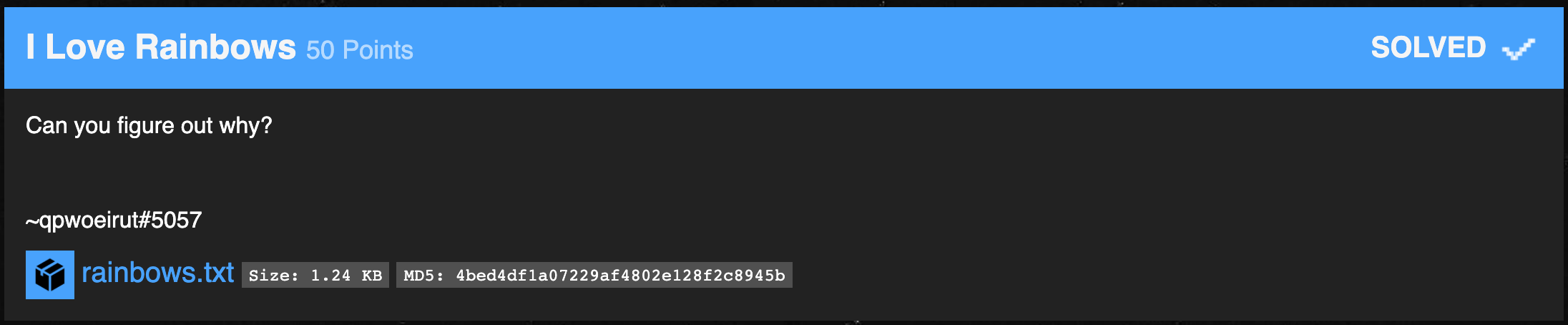
This leaves only time for the more basic, top of the category challenges, but hey I’ll be happy with that.
I love Rainbows
Whenever I see the word rainbow in a hacking context, rainbow tables immediately come to mind, and with it MD5 hashes.
The challenge has an attached file of what looks like… yup you guessed it, MD5 hashes.
Cracking MD5 hashes is trivial in this day and age, so I opted to see if I could find a website that would do it for me.
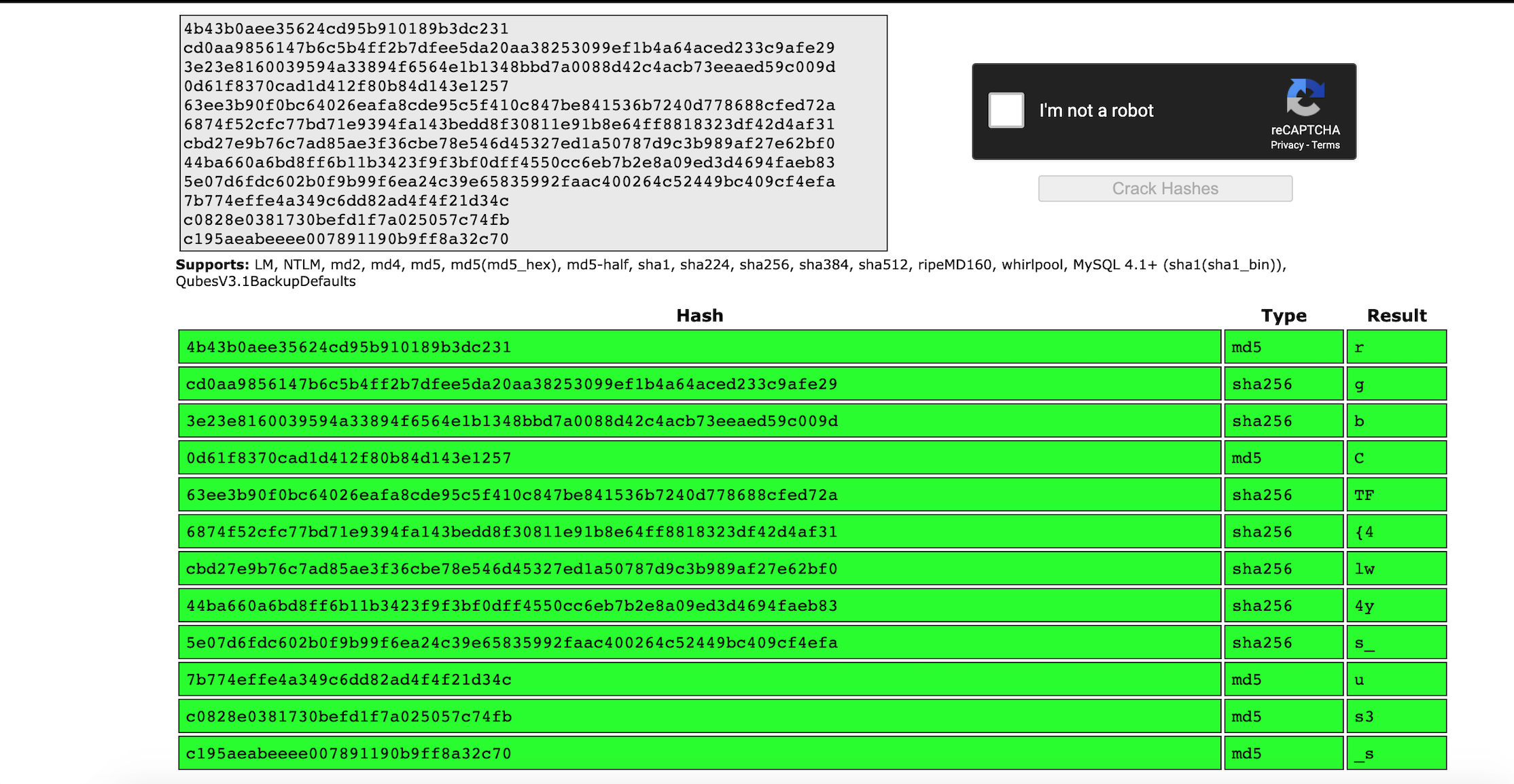
The hash-cracker can only handle 20 lines at a time, but thats fine since its immediately apparent that my hunch was correct.
One more quick paste into the hash-cracker and that leaves us with rgbCTF{4lw4ys_us3_s4lt_wh3n_h4shing}
Conclusion
Spending a little bit of time thinking outside the box for this CTF was alot of fun. Normally I dont have cause to step through Javascript with the debugger, so that was a fun thought exercise.
Next time I’ll have to set aside more dedicated time for CTF, it would be great to solve some Pwn/Rev category challenges or actually get through one of the more advanced web challenges.
Ultimately by myself with just a few hours I managed to wind up at 547 out of 1337, which is kind of meh but cool considering the kind folks at RGB Sec are giving Shodan to the top 1000 placing teams.
