Intro
Continuing with my efforts of becoming better at CTFs I decided to participate in the SANS Holiday Hack Challenge. It is a pretty awesome challenge with a lovely pixelated game accompanying the tasks. It takes place in the North Pole and the gist of it is Santa is missing. The elfs were all kinds of helpful providing articles related to some of the tasks. I learned alot about some neat topics that I had little experience with, such a Android application Reverse Engineering and Password Cracking.
Task 1
Lets take a look at task one.
- What is the secret message in Santas tweets?
- What is inside the ZIP file distributed by Santas team?
Well to start with lets spin up the game and hop in. We are greeted with a scene involving 2 NPCs that explain Santa is missing, as well as his business card.

Pretty easy to see what we need to do. Lets start with Twitter first. This task was actually a bit of a pain because I do not have a Twitter or IG so viewing the content required making them.
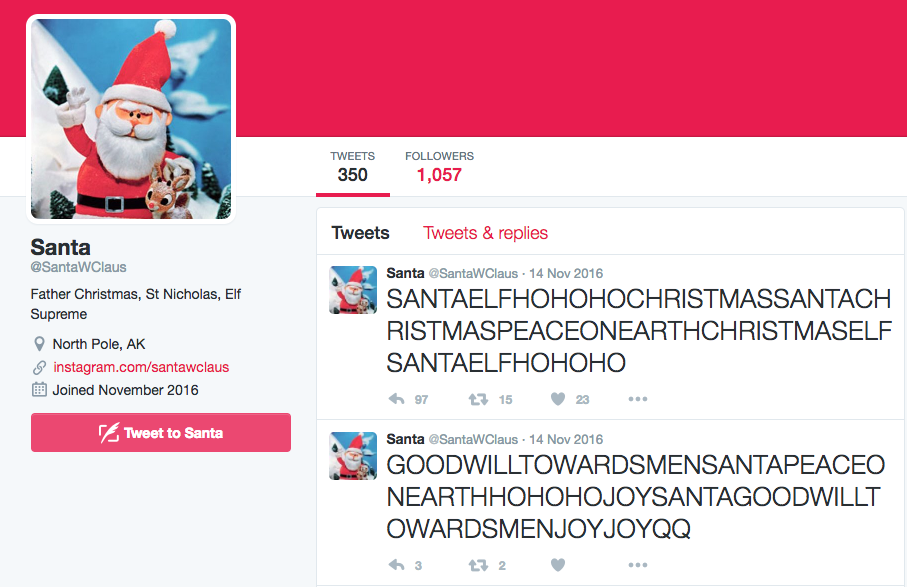
We can see Santas tweets look a little cryptic, and after scrolling through them a pattern seems apparent. From here I thought web scraping would be something fun to try, so I cobbled together a script to append all of Santas tweets together. I know the code could look better but I only needed this to work once so I didnt put alot of effort into it. The Tweepy library really came in handy here to access Twitters API.
|
|
Its quick, dirty, and gets the job done. So lets look at the results and see what we get.
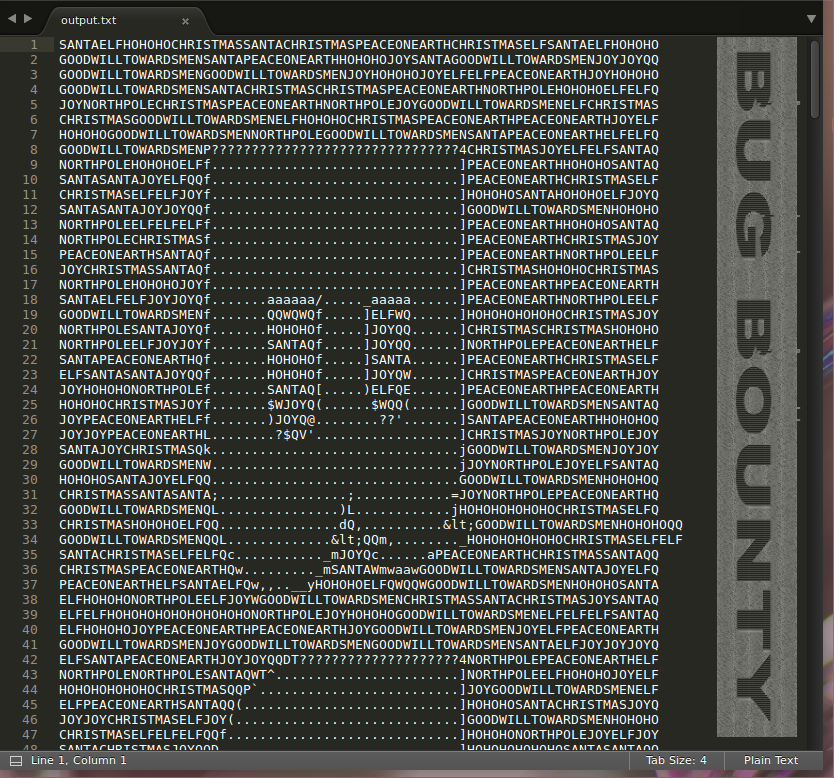
Alright so we got the answer ‘Bug Bounty’ from the tweets, but what do we do with that? Well there was a second part to task 1, the zip. I think if we move on to the IG account we can figure out where to go.
A quick look at the IG and we quickly find the topic of interest. A picture of Santas desk. This especially I found great because it hammers home a great point about opsec, never post pictures of your work desk or environment to social media.

Look at the picture we can easily spot a filename in the web browser, and a url off to the right near an nmap reference. If we tack these two tidbits together and drop www.northpolewonderland.com/SantaGram_v4.2.zip into the browser we are rewarded with a zip file.
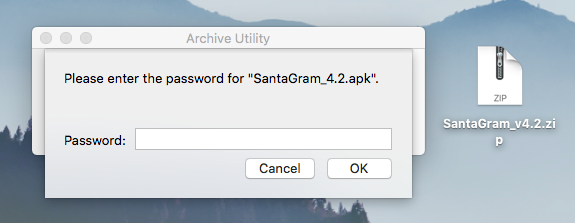
I wonder what the password could be…. maybe… bug bounty? Dropping that in rewards us with the second answer to task 1. SantaGram_v4.2.apk.
- What is the secret message in Santas tweets? - Bug Bounty
- What is in the zip file being distributed by Santas team? - SantaGram_v4.2.apk
Task 2
Having cleared the hurdles of task 1, lets get started on task 2.
- What username and password are embedded in the apk file?
- What is the name of the audio component (audio file) in the Santagram APK file?
Alright so this one was definitely a journey for me because when you say ‘Reverse Engineering Android Applications’ it sounds kind of daunting. But thankfully my good pals youtube and google have my back. With about 30 minutes of googling and videos, as well as the article from the elf at the Northpole, I was able to get the application reversed. Heres how I went about it.
- The elf said an apk is just a zip file, so we rename it .zip and look at the contents. We see a binary manifest. Lets see if we can take care of that.
I used Kali Linux for this part just because it came with many of the recommended tools.

So here we see apktool and dex2jar. Apktool is going to reverse that manifest and give us some smali files, and dex2jar is going to take the dex files and give us the class files so we can view them as if there were almost the original java code.
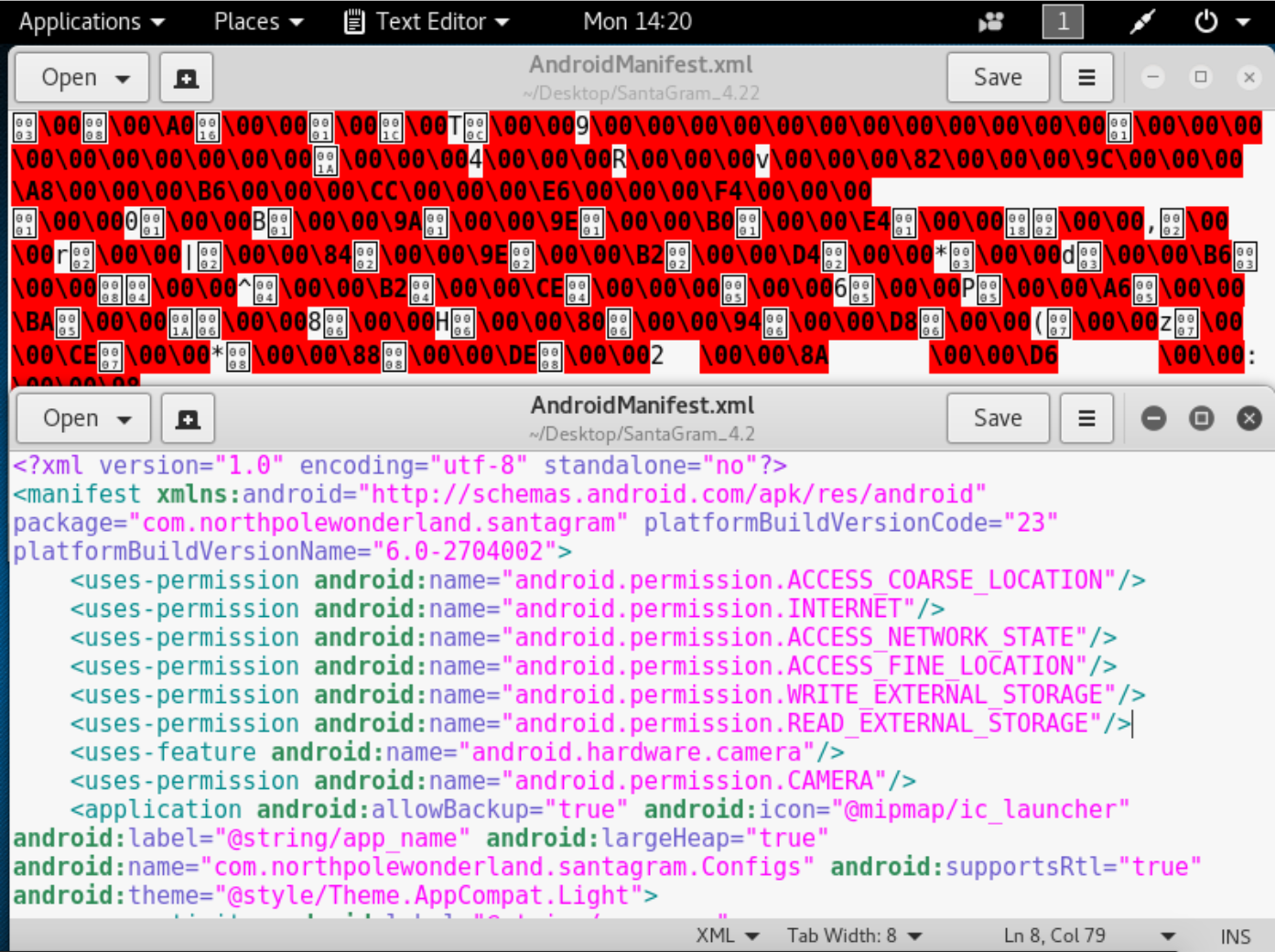
Alright so we got the manifest reversed which gives some useful information from an oversight, but there is no sign of any embedded credentials. Lets look at what dex2jar gives us next.
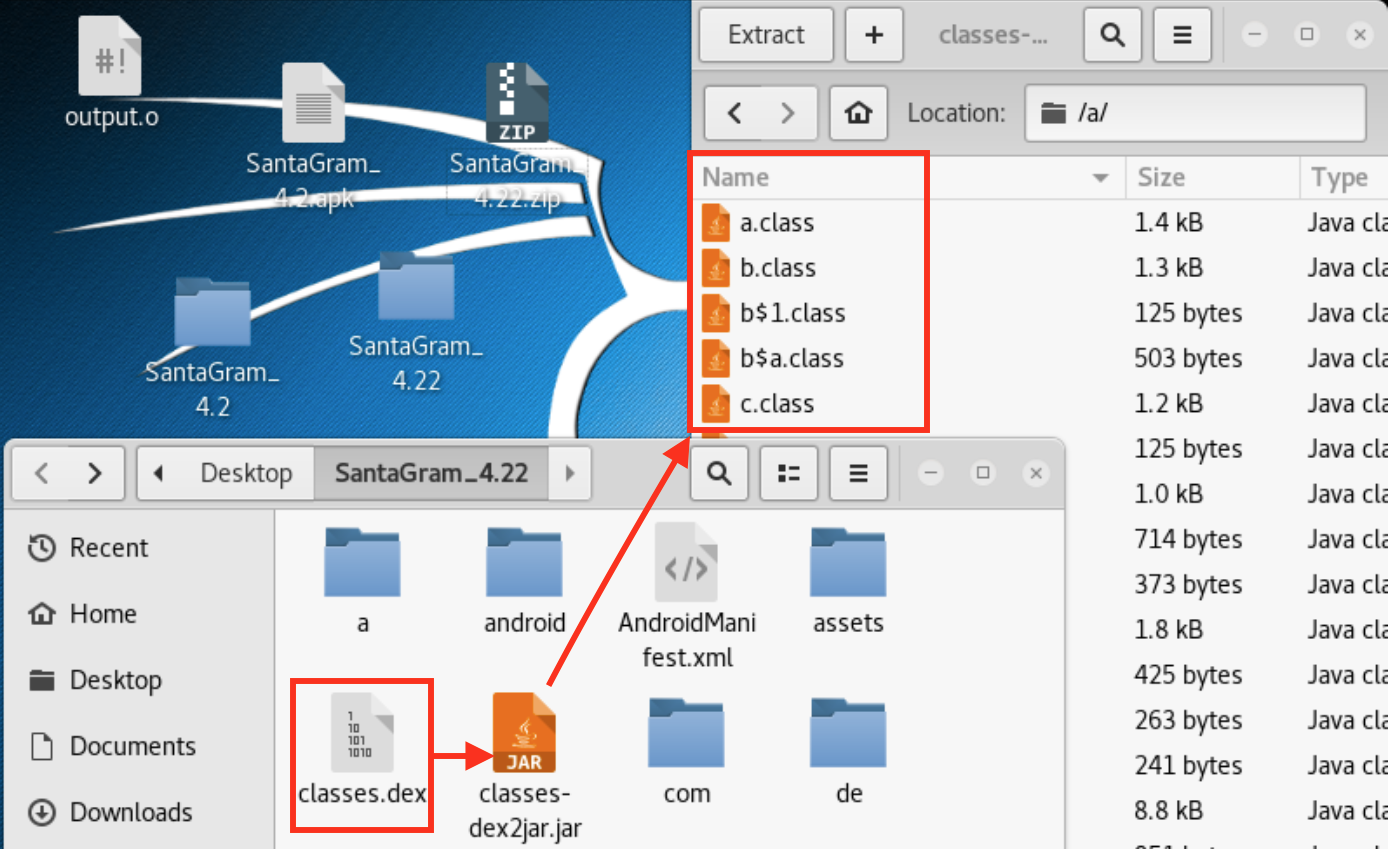
So here we can see dex2jar making our dex files readable. The elf at the Northpole suggested Jad-X but I went with JD-Gui. It took me a relatively short time to pull the git repo and launch the gui. With JD-Gui I was able to look at the class files that dex2jar converted. Thanks to a search bar at the top of the window I was able to just search for username and there we had our answer.
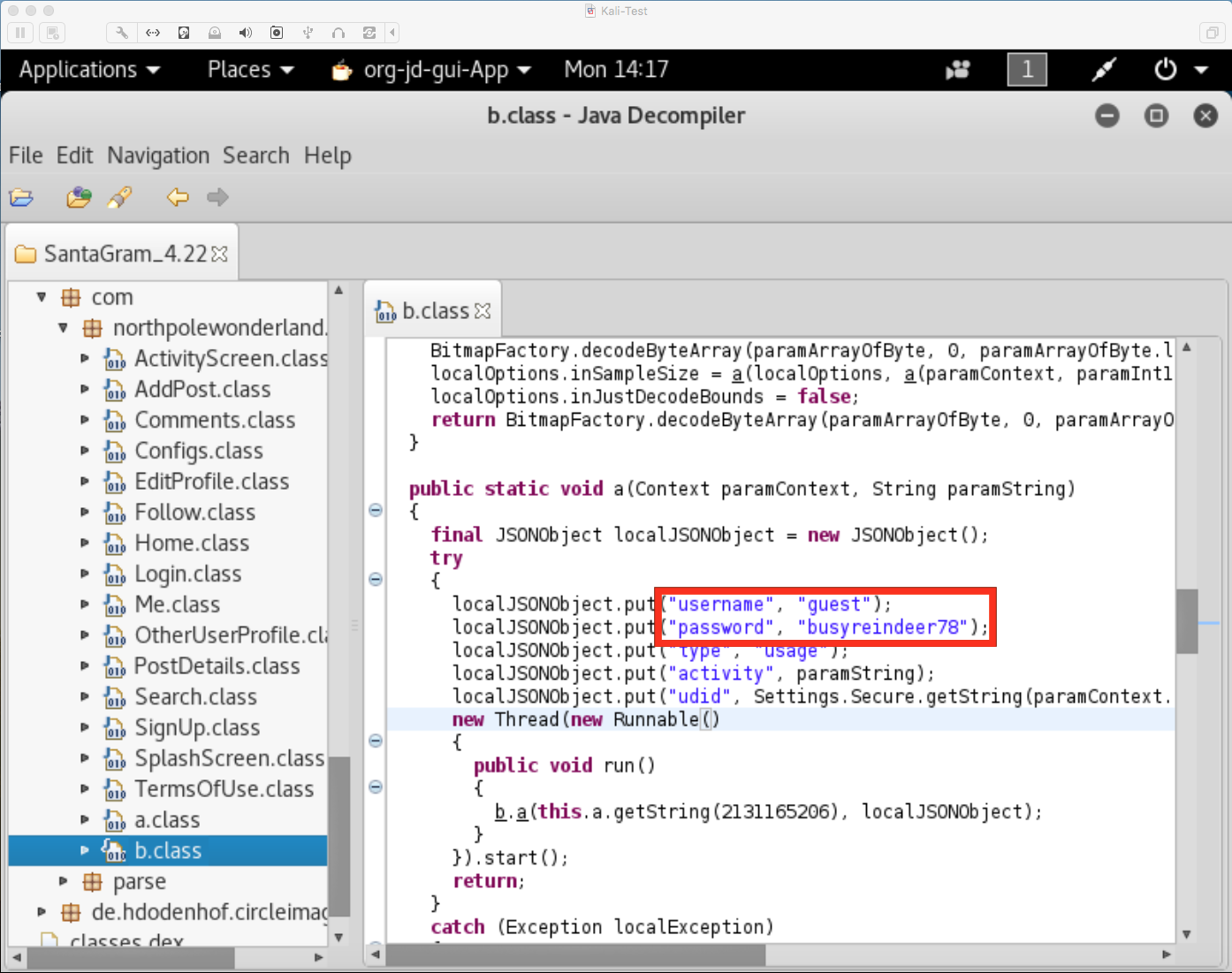
And there we have it, the credentials we wanted.
Additioanlly, I could have showed the exact commandline usage and syntax that I used on aptktool or dex2jar, but frankly its really easy to just do -help and figure it out.
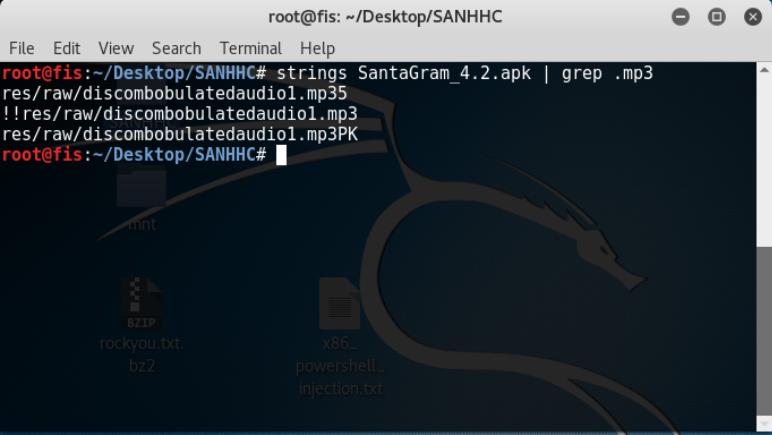
Alright so the last part of task 2 is the audio file. I figured the name would be stored somewhere in the apk but I didnt have a good approach to finding it. So I just ran strings on the file and grepped for things ending in .mp3. Fortunately it paid off.
In summary:
- What username and password are embedded in the APK file? * guest, busyreindeer78 *
- What is the name of the audible component (audio file) in the SantaGram APK file? discombobulatedaudio1.mp3
Task 3
I realize this writeup is getting a little long, fortunately as far as keeping it short goes, this is where I am about out of time.
Part of the game has you searching the NorthPole for the five pieces to a * cranberry pi *
Upon completing this search we are rewarded with a cranpi.img file. Which brings us to this next part.
- What is the password for the “cranpi” account on the Cranberry Pi system?
Well fortunately one of the elfs provided a lovely article on mounting the .img file by determining the number of bytes to get to the start of the Linux file system.
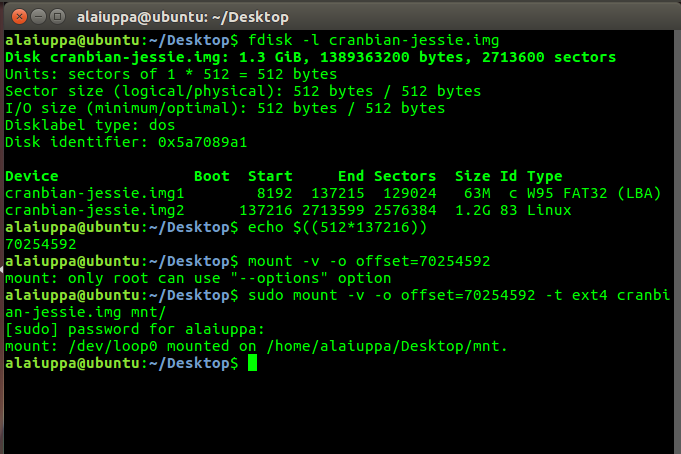
Looks like were in without issue.
And of course we can verify this by cat /etc/shadow and making sure the cranpi account is there.
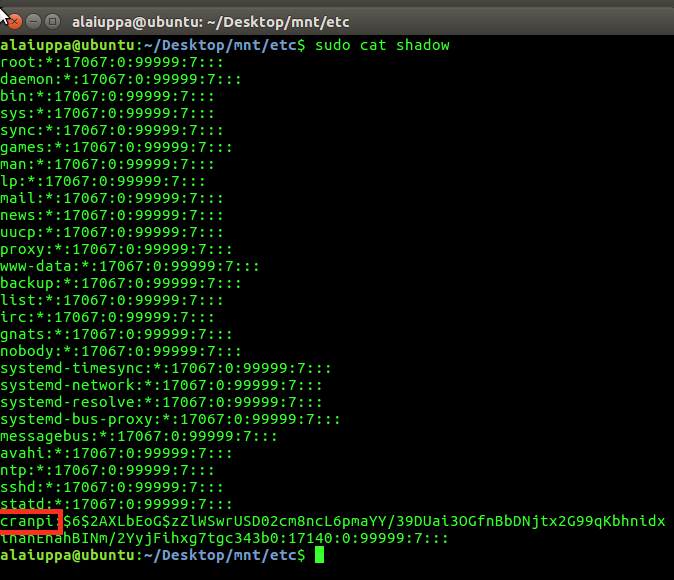
So if youre unfamiliar with what we are looking at, it is the password hash of the cranpi account. Because storing passwords in plaintext is bad, I really shouldnt have to explain that.
Knowing what to do next is simple because the elfs were helpful in pointing it out, but Im going to supply a brief summation.
A hash is an algorithm that produces a unique value of the input passed through. It has many uses from verifying file integrity to storing passwords. Well by using this algorithm, our program John the Ripper, will enumerate through a list of passwords, hash them, and see if any hashes match the one we have. Since all hashs are meant to be unique, a match would mean we have the password.
The elfs told us to use the rockyou.txt wordlist with john, so lets do just that.
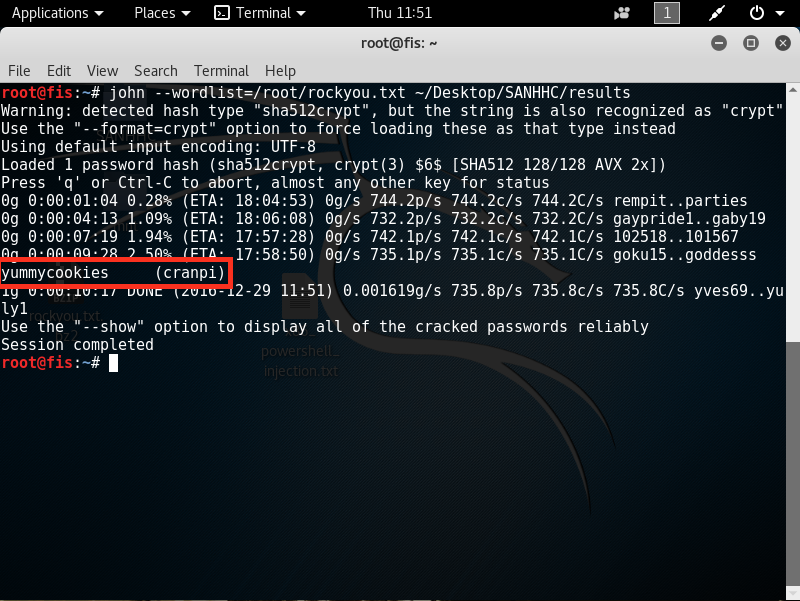
Worth mentioning is that since I had both the shadow and passwd file I went ahead and ran unshadow on them. Unshadow combines the two files so John can use them.
John made short work of that, only taking about ten minutes and that gives us the answer to our question.
- What is the password for the “cranpi” account on the Cranberry Pi system? * yummycookies*
Summary
As a result of this challenge I got to explore some concepts I havent gotten into before, such as reversing the android app. Additionally it was great in providing guidance to help me implement all of this new information.
I got the opportunity to
- Find a use for my knowledge of web scraping
- See a great example of why you shouldnt take pictures of your desk, opsec!
- reverse an android app and point out why you shouldnt embed creds
- run strings and actually get a useful result, thanks grep
- learn how to mount a linux file system from a .img, great for forensics
- work with john the ripper, i hadnt done this before either
I had alot of fun with this challenge and I look forward to more future CTFs.
I hope you enjoyed reading this, thanks for taking the time!